LockBit Leak Provides Insight into Ransomware-as-a-Service (RaaS) Enterprise

On May 7, 2025, the LockBit ransomware group suffered a major breach of its internal infrastructure, marking one of the most significant exposures of a ransomware operation to date. The attackers defaced LockBit’s dark web admin and affiliate panels and leaked a database containing thousands of negotiation messages, Bitcoin wallet addresses, affiliate credentials, and operational details. This incident follows previous law enforcement actions targeting LockBit, including Operation Cronos in February 2024.
Verified by multiple security researchers, this leak offers a rare window into the inner workings of a ransomware-as-a-service (RaaS) enterprise. While the identity of the attackers remains unknown, the breach not only compromises LockBit’s operational security but also presents valuable intelligence for defenders and law enforcement alike.
Key takeaways
- Although the LockBit panel breach exposed approximately 62,400 Bitcoin addresses, only 49 showed evidence of transaction activity
- Among the affiliate monikers exposed in the chat logs, Christopher stands out as the most operationally active, while Swan emerges as the most financially successful based on observed transactions
- Funds attributed to administrator-controlled wallets continue to remain dormant for extended periods after receiving 20% split of victim funds
- Despite a sharp drop in activity throughout 2025, LockBit appears to be continuing efforts to recruit new affiliates and sustain its operations
Who is LockBit?
LockBit is a ransomware-as-a-service (RaaS) operation that first appeared in 2019 and swiftly rose to become one of the most widespread and damaging ransomware groups globally. Its business model centers on leasing its ransomware infrastructure — including malware, payment portals, and leak sites — to affiliates who carry out attacks. These affiliates encrypt victim data and demand ransom payments, often using double extortion tactics by threatening to leak stolen data. By 2022, LockBit had become the most widely deployed ransomware variant in the world, according to the US Cybersecurity and Infrastructure Security Agency (CISA), and had been linked to over 2,000 attacks across sectors such as healthcare, education, and critical infrastructure. The group’s cumulative ransom demands have reached into the hundreds of millions of dollars.
In February 2024, a major international law enforcement effort — Operation Cronos — was launched to dismantle LockBit’s infrastructure. Coordinated by the UK’s National Crime Agency (NCA) alongside the FBI, Europol, and partners from over ten countries, the operation resulted in the seizure of LockBit’s dark web leak site, affiliate portals, and 34 servers in multiple jurisdictions. Authorities also froze more than 200 cryptocurrency wallets, dismantled 14,000 rogue accounts, and acquired critical intelligence, including LockBit’s source code, internal communications, and decryption keys. During the operation, two affiliates were arrested in Poland and Ukraine, and indictments were unsealed in the US against Russian nationals Artur Sungatov and Ivan Kondratyev (also known as “Bassterlord”), the latter of whom allegedly developed attack tools and participated directly in ransomware campaigns.
Building on the intelligence gained from Operation Cronos, in May 2024, US and UK authorities formally unmasked Dmitry Khoroshev, known by the alias “LockBitSupp,” as LockBit’s primary administrator and architect. He was charged with a 26-count indictment and named as the target of a USD 10 million reward for information leading to his arrest. These developments marked a turning point in the global response to ransomware, exposing the leadership of one of the most operationally successful cybercrime enterprises to date.
Overview of breach
On May 7, 2025, the LockBit ransomware group suffered a significant breach of its dark web infrastructure. Their affiliate and admin panels were defaced with the message: “Don’t do crime. CRIME IS BAD xoxo from Prague,” accompanied by a link to download a MySQL database dump titled paneldb_dump.zip.

The leaked database, reportedly created around April 29, 2025, contains extensive details about LockBit's operations, including nearly 62,400 unique Bitcoin wallet addresses used for ransom payments, over 4,400 negotiation messages between LockBit operators and victims from December 2024 to April 2025, details of custom ransomware builds for specific attacks, and a user table listing 75 administrators and affiliates with plaintext passwords.

LockBit has acknowledged the breach but claimed that only a "light panel" was compromised, asserting that no decryptors or stolen company data were affected.
The identity of the attackers remains unknown. However, the defacement message mirrors one used in a recent breach of the Everest ransomware group's infrastructure, suggesting a possible connection or a trend of targeting ransomware groups by rival actors or vigilantes.
This breach not only undermines LockBit's reputation but also provides a wealth of information that could aid in tracking down affiliates, understanding ransomware operations, and developing more effective countermeasures against such cyber threats.
Affiliate profiles
Approximately 75 unique monikers were identified in the leaked LockBit data, many of which reflect a range of distinct personalities and communication styles. Based upon the chat logs, the top five most active affiliate profiles were identified as “Christopher,” “Lofikdis," “Swan,” “PiotrBond,” and “JamesCraig.”
1. Christopher
- Message count: 2,078 (most active)
- Estimated earnings: USD 196,240
Christopher exhibits a businesslike, process-driven communication style, combining structured pricing enforcement with transactional flexibility and detailed technical support. While uncompromising on deadlines and bottom-line demands, he avoids overt aggression and instead leans on trust-building language, professionalism, and methodical follow-through. Among LockBit affiliates, Christopher stands out as one of the more polished and commercially savvy operators, likely contributing to his success in extracting a higher volume of ransom payments.
Christopher is the only affiliate who consistently sends their 80% share directly to a VASP following the initial victim payment.
.jpg)
2. Lofikdis
- Message count: 470
- Estimated earnings: USD 4,827
Lofikdis communicates with a blunt, minimally polished, and often defensive tone, relying heavily on canned explanations, vague technical claims, and repeated deferrals to an unresponsive “boss.” While they follow standard LockBit procedures (test decryption, BTC wallets, scripted instructions), their style is marked by reactive stress, poor crisis management, and inconsistent professionalism.
.jpg)
3. Swan
- Message count: 357
- Estimated earnings: USD 1.6 million

Swan's communication style can be characterized as one of calculated coercion. Their approach to negotiation is marked by the deliberate use of psychological pressure, elevated ransom demands, and rigid terms. Swan strategically leverages urgency, reputational threats, and the involvement of downstream victims to compel payment, all while maintaining a superficial layer of professionalism through standardized responses and minimal technical assistance.

4. PiotrBond
- Message count: 290
- Estimated earnings: USD 10,373
PiotrBond attempts to balance intimidation and customer service, delivering threats alongside step-by-step instructions, price negotiation, and technical support. This hybrid style reflects LockBit’s professionalized RaaS model, likely aiming to instill fear, ensure payment, and maintain a reputation for “reliable” service among victims.

5. JamesCraig
- Message count: 290
- Estimated earnings: USD 1,324
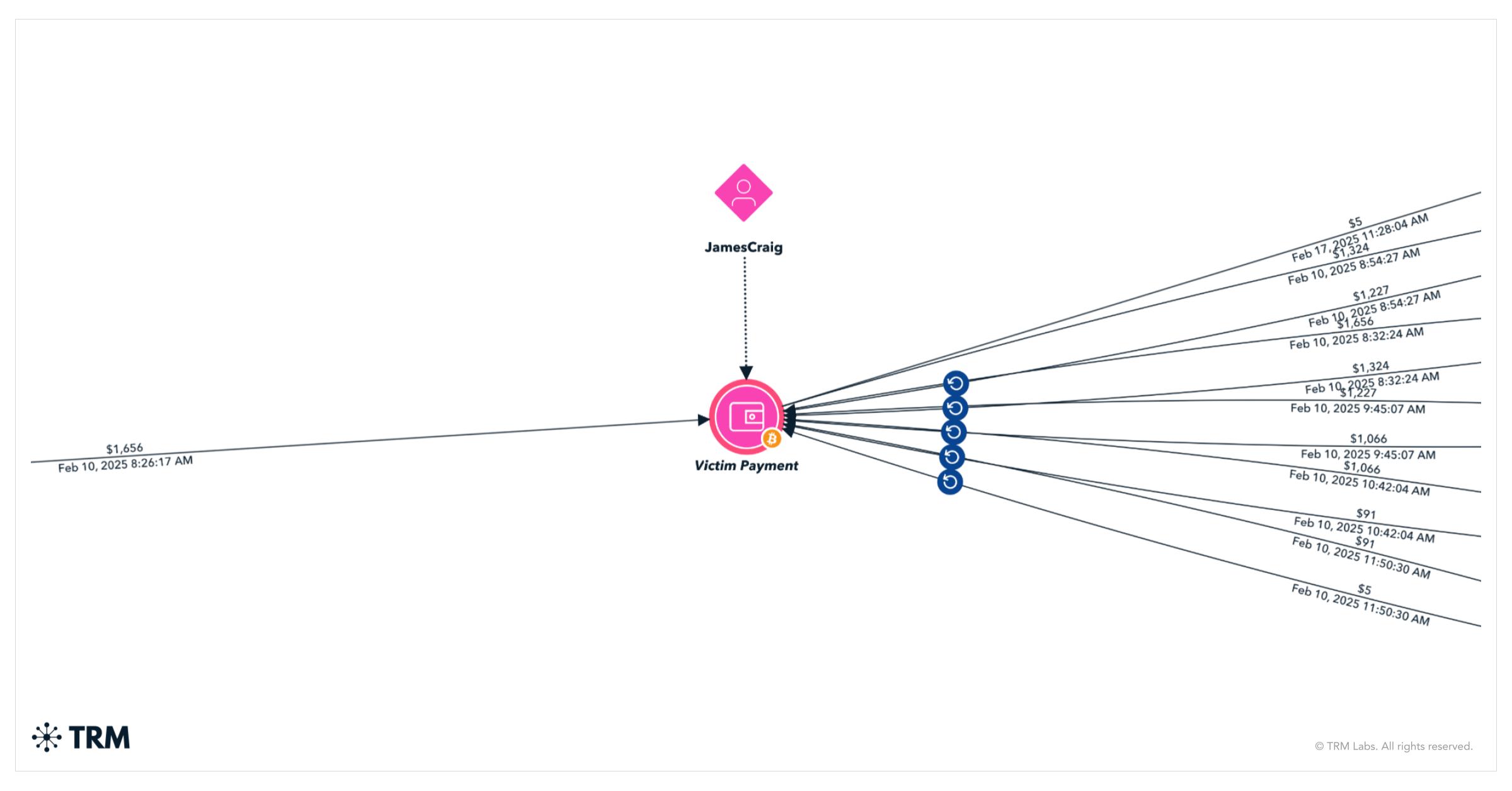
JamesCraig communicates like a commission-driven operator within a ransomware-as-a-service model: impatient, profit-focused, and largely desensitized to victim concerns. JamesCraig will occasionally feign discounts but only after increasing the agreed upon price. The style blends mechanical customer service with price enforcement, suggesting an affiliate who views each negotiation as a repeatable transaction rather than a unique engagement.

Within the chat logs, Christopher and JamesCraig report that access to the LockBit panel is priced at approximately USD 777. Based on these claims and supporting on-chain analysis, 12 Bitcoin addresses were identified as likely payments made by prospective affiliates seeking access to the panel. Despite the drastic decline in activity from LockBit throughout 2024 and into 2025, the group appears to still be actively recruiting affiliates and carrying out attacks.
During a specific negotiation, an individual from within the victim organization appeared to inquire about how to gain access to the LockBit panel — either as an attempt to earn personal profit or to gather intelligence on the group. In response, Christopher provided details on how prospective affiliates can obtain access to the platform.



After analyzing confirmed victim payments on-chain, it became clear that administrator-controlled funds were consistently transferred to designated addresses immediately after the initial payment — where they have remained inactive ever since.

Conclusion
The May 2025 LockBit panel breach provides valuable insight into the internal operations of a major ransomware-as-a-service group. The leaked data — including affiliate communications, wallet addresses, and panel access mechanisms — offers a clearer picture of how LockBit functions on both a technical and organizational level. While the group continues to operate in some capacity, this breach represents a notable disruption to its infrastructure and exposes patterns that may inform future investigations and defense strategies. As ransomware threats continue to evolve, the findings from this incident can support broader efforts to understand and mitigate the impact of RaaS ecosystems.
Access our coverage of TRON, Solana and 23 other blockchains
Fill out the form to speak with our team about investigative professional services.
















